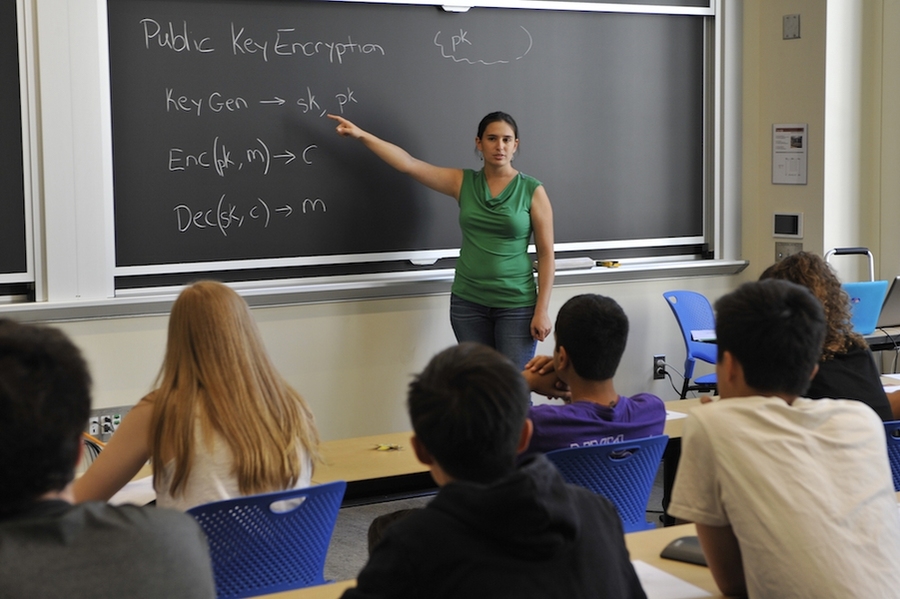"Split up into groups of three," directed Sophia Yakoubov, associate staff in the Secure Resilient Systems and Technology Group at MIT Lincoln Laboratory and instructor of the LLCipher cryptography workshop. "Within each group, the person sitting on the left is Alice, the person on the right is Bob, and the person in the middle is Eve. Alice must write a secret message in a notebook and pass it to Bob. Eve must figure out Alice's message and intercept everything that Alice and Bob pass to each other. Alice and Bob each have a lock and matching key, however, they cannot exchange their keys. How can Alice pass her secret message to Bob so that Eve is unable to unlock and view the secret, and only Bob can read it?"
The 13 high school students participating in the workshop glanced at one another until one brave student addressed the entire class, starting a flurry of conversation: "Any ideas?"
Thus began one of the many hands-on challenges that students tackled at the LLCipher workshop held in August at the MIT campus in Cambridge, Massachusetts, and MIT Lincoln Laboratory in Lexington, Massachusetts. LLCipher is a one-week program that introduces students to modern cryptography, a theoretical approach to securing data such as Alice’s secret message. The program begins with lessons in abstract algebra and number theory that students use to understand theoretical cryptography during lessons later in the workshop.
"I decided that LLCipher was for me when I researched the course topics," says student Evan Hughes. "As I made my way down the topic list, I didn’t understand many of the concepts, so I immediately applied to the program."
Because of student feedback from LLCipher's inaugural year in 2015, Yakoubov extended each lesson from two to six hours. "Many students said they wanted more time on learning," says Yakoubov. "Specifically, they wanted to learn more than one cryptography technique and apply those techniques to 'real-world' scenarios, rather than just learn theory." This year, in addition to the El Gamal public key cryptosystem, students learned the RSA public key cryptosystem. RSA is one of the most common methods to secure data and uses slightly different math from El Gamal. Both RSA and El Gamal use modular arithmetic, a type of math in which integers "wrap around" upon reaching a certain value, i.e., the modulus, similar to a clock that uses 12 numbers to represent 24 hours in one day. El Gamal uses a very large prime number as a modulus; RSA uses a very large composite number, i.e., a whole number that can be divided evenly by numbers other than 1 or itself, with a secret factorization.
To reinforce the techniques and allow students to apply the theory, Yakoubov, along with the help of Uri Blumenthal and Jeff Diewald of the Secure Resilient Systems and Technology Group, created an online platform that includes El Gamal- and RSA-based challenges. "With these exercises, we are able to show students examples of flawed cryptography so that they can see how easily it can be broken," says Yakoubov. "Students can visualize huge numbers and see why concepts like randomization are so important to effective encryption." The platform is used throughout the course and includes six challenges that bolster teamwork and creativity.
"Learning about public key encryption is fun because it is so complicated and secretive," says student Garrett Mallinson. "I like creating codes that no one else can break or unlock — this is like what characters do on television shows in just 45 minutes."
During the final day of the course, students toured several Lincoln Laboratory facilities, such as the anechoic chambers and the Flight Test Facility. "I enjoyed the tour around Lincoln Laboratory," says Hughes. "We always hear about theoretical concepts at school, so it is inspiring to see people applying and making the things we hear about."
After the tour, students listened to a guest lecture from Emily Shen of the Secure Resilient Systems and Technology Group on a more specialized cryptography topic. Shen explained secure multiparty computation, a tool that allows multiple users with secret inputs to compute a joint function on their inputs without having to reveal anything beyond the output of the joint function. To demonstrate the concept, students participated in an activity to find out whether the majority of the group likes pie or cake without each student revealing his or her preference. First, the group assigned pie and cake a binary representation — 0 for pie and 1 for cake. The group also picked a modulus larger than the size of the group; in this case, the modulus was 14. The first participant secretly chose an auxiliary value between 0 and 13, added his vote, 0 or 1, to that value, and then used modular arithmetic to get a new value. For example, if he chose an auxiliary value of 13 and his vote was 1, he took the remainder modulo of 14 to get a total of 0. He then passed on the sum to the next student. This pattern continued until the last student gave her value to the original participant, who then subtracted the secret auxiliary number from the last value. The remaining value represented the amount of votes for cake and indicated whether the majority of the group likes cake or pie.
"Cryptography is a tool that is very important. It's an interesting intersection of math and computer science to which people are not often exposed," says Shen. "I want kids to learn about this field and hopefully find it exciting." Yakoubov found that the students benefited from the new features, particularly the applied challenges, of the LLCipher program. She hopes that students realize that math can be fun and can be applied to complex and exciting real-life problems.
Following the program, students indicated that they were interested in taking computer science courses in college and hope to aim for careers in science, technology, engineering, and math fields. "LLCipher helped us understand the cryptography-based concepts that we see in our everyday lives, such as encryption messages and functions on our personal computers," says student Brandon Chu. "At the end of the program, everything came together and made sense, which was really exciting. We were doing things that seemed impossible at first glance. I definitely feel smarter and more empowered now than when we started."